Article -> Article Details
| Title | What Is XSS Attack? |
|---|---|
| Category | Computers --> Security |
| Meta Keywords | cybersecurity coe, centre of excellence hyderabad, cyber security hyderabad, cyber security telangana, Cybersecurity Incubation centre, Cybersecurity Academia and R&D Centres, cloud computing vs cyber security, cyber security challenges in india |
| Owner | Cybersecurity |
| Description | |
|
The process of an XSS attack begins with the attacker identifying a vulnerability within a web application that either does not properly sanitise user input or incorrectly handles data within the Document Object Model (DOM). The attacker then creates a malicious script to exploit this vulnerability. When the script is executed, it can perform actions on behalf of the user, manipulate web content or steal information, all without the user's consent or awareness. Exploring The Types Of XSS AttacksReflected XSS: This type occurs when an attacker sends a crafted URL containing malicious script to a user. When the user clicks on the link, the web application receives the malicious data as input and reflects it back in the response. The browser then executes the script because it appears to be coming from a trusted source. Reflected XSS requires the victim to actively click on a malicious link and is only effective for the duration of a single session. Stored XSS: Unlike reflected XSS, stored XSS involves the malicious script being saved on the web server, such as in a comment, forum post or in user-generated content. This script is then served to every user who accesses the stored content. Stored XSS is particularly dangerous because it can affect many users and does not require the victim to take any action like clicking on a link. DOM-based XSS: In this type, the vulnerability is in the client-side code rather than the server-side or the input itself. The attack occurs when the webpage’s JavaScript takes data from user inputs (like URL parameters) and dynamically writes it to the DOM without proper sanitisation. The user’s browser then executes the full page including the malicious script that has been added to the DOM. This type of XSS attack occurs entirely on the client side. Ripple Effect Of XSS AttacksXSS attacks manipulate trusted web applications to execute unauthorised commands or reveal confidential information. This manipulation undermines user trust and can lead to the compromise of entire systems. For users, the consequences are often severe, including loss of sensitive data like personal information, banking details and passwords. For systems, XSS can lead to unauthorised access, data breaches and a degradation of user experience and system functionality. Here are some potential risks and consequences of an XSS exploit: ● Stealing Cookies ● Session Hijacking ● Phishing ● Malware Distribution ● Defacement Unmasking XSS And Identifying Its Vulnerabilities
Insufficient Input Validation and Sanitisation: Many XSS vulnerabilities stem from the application’s failure to rigorously validate or sanitise user inputs. Inadequate Output Encoding: Applications that do not encode or escape outputs effectively allow attackers to inject executable code into web pages, which the browser then processes as part of the page. Poorly Configured Security Headers: Security configurations that do not restrict the types of content that can be executed can leave a website vulnerable to XSS attacks. Lack of Segregation between Data and Code: Web applications that fail to keep user data separate from code can easily be manipulated into executing that data as if it were code. To ensure the security of a website or application, it’s crucial to understand what is XSS attack, identify and mitigate potential vulnerabilities that could lead to XSS attacks. Here are some tools and methods that can be used for this purpose: ● Static Application Security Testing (SAST): Tools like Checkmarx, Fortify, and Veracode analyse source code to detect security vulnerabilities, including those that could lead to XSS attacks, without needing to run the application. ● Dynamic Application Security Testing (DAST): Tools such as OWASP ZAP, Burp Suite, and Acunetix simulate attacks on a running application to identify vulnerabilities dynamically. ● Security Headers Analysis: Tools like SecurityHeaders.com allow developers to analyse the HTTP security headers sent by their web applications. Safeguarding Against XSS AttacksTo safeguard web applications against XSS attacks and avert substantial security breaches, developers must adopt robust preventive measures. By adhering to these guidelines, developers can significantly bolster the security posture of their web applications, mitigating the pervasive threat of XSS attacks.: ● Input Validation and Sanitisation: Thoroughly validate and sanitise user inputs, employing tools like OWASP’s AntiSamy or the Java Encoder for comprehensive protection. ● Leverage Secure Programming Frameworks: Embrace frameworks such as React, Angular, or Vue.js, which inherently escape HTML, thwarting XSS threats effortlessly. ● Implement Content Security Policy (CSP): Enforce strict controls over resource loading within the browser to effectively counter XSS incursions. ● Harness Secure HTTP Headers: Activate headers like X-Content-Type-Options: no-sniff and X-Frame-Options to fortify your defenses against XSS-related vulnerabilities. For advanced XSS defense: ● Employ Encoding Strategies: Encode output data meticulously, including HTML, JavaScript, and URLs, to prevent malicious script execution effectively. ● Handle User Input Across Contexts: Ensure meticulous validation, sanitization, and context-aware encoding to neutralise potential code execution risks. Effective Testing And Maintenance Practices
Additionally, manual techniques such as skilled penetration testing and comprehensive code reviews complement these strategies. Regular security audits and patch management are vital for ongoing protection. Staying updated on XSS threats ensures timely adaptation of defenses. Educating developers and content creators about XSS risks is crucial through training programs and clear guidelines on secure coding practices. Regular communication about evolving threats fosters a security-conscious culture. Engaging developers in security-focused activities reinforces security concepts effectively. ConclusionCross-Site Scripting (XSS) attacks pose a significant threat in the digital world, necessitating robust cybersecurity measures. XSS vulnerabilities, leading to data breaches, unauthorised access and financial loss, can be exploited through Reflected, Stored and DOM-based attacks. Defending against XSS involves proactive coding, secure programming frameworks and security configurations. Regular testing, maintenance and security audits are crucial to keep defences updated against emerging threats. As digital interactions grow, so does the responsibility to secure web environments. Comprehensive XSS defences, diligent maintenance and an informed development community can help organisations protect against XSS threats. | |

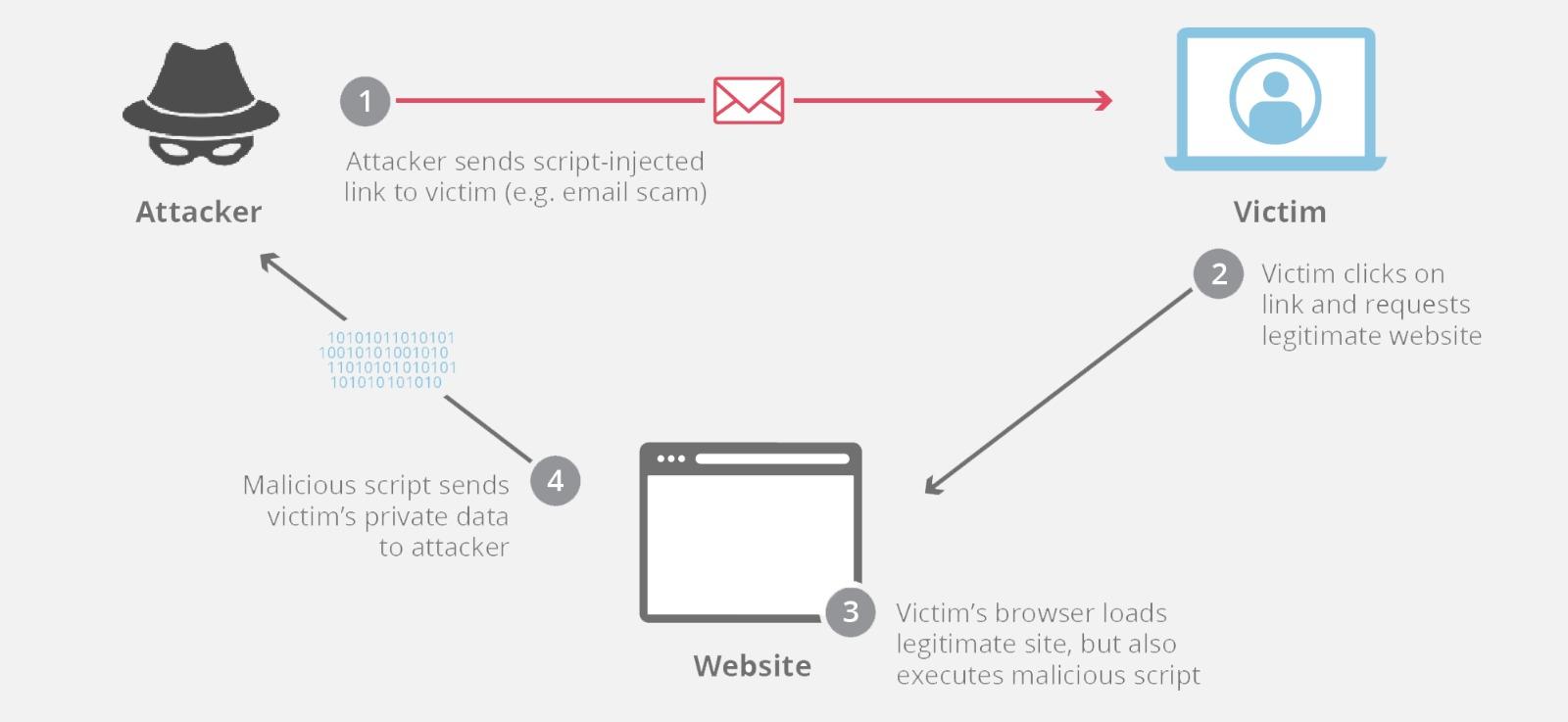
 XSS attacks pose a significant threat to web applications, exploiting vulnerabilities that allow hackers to inject malicious scripts into web pages viewed by other users. Here are some common vulnerabilities that lead to XSS attacks:
XSS attacks pose a significant threat to web applications, exploiting vulnerabilities that allow hackers to inject malicious scripts into web pages viewed by other users. Here are some common vulnerabilities that lead to XSS attacks: Ensuring robust XSS defenses requires a blend of automated and manual testing methods. Automated tools like Dynamic Application Security Testing (DAST) and Static Application Security Testing (SAST) tools, adept at detecting XSS vulnerabilities, play a crucial role.
Ensuring robust XSS defenses requires a blend of automated and manual testing methods. Automated tools like Dynamic Application Security Testing (DAST) and Static Application Security Testing (SAST) tools, adept at detecting XSS vulnerabilities, play a crucial role.