Article -> Article Details
| Title | Securing Cloud-Native Applications: A Journey into Robust Cloud Security |
|---|---|
| Category | Computers --> Security |
| Meta Keywords | Enterprise SaaS Services, Cloud Solution, Data Analytics & AI Solution, Cybersecurity Solution, Digital Experience Services, Enterprise Vulnerability Management, Cloud First Business Strategy |
| Owner | stldigital |
| Description | |
| In today’s digital landscape, cloud-native applications have become the backbone of modern software development. These applications leverage the power of cloud computing offered by cloud service providers to deliver scalable, resilient, and flexible solutions. However, as cloud environments grow more complex, ensuring robust security becomes a paramount concern.
Note:- In this blog, we will explore how cloud-native applications strive to fortify their security measures, leveraging a combination of best practices and powerful tools provided by cloud platforms like Google Cloud Platform (GCP). Join us on this exciting journey into the realm of cloud security. Cloud-Native Applications and SecurityCloud-native applications are designed to fully leverage the capabilities of the cloud, enabling organizations to build and deploy applications faster and more efficiently. But how do they ensure the security of their cloud-native infrastructure and protect sensitive data? Do the best cloud service providers in USA ensure the same? Let’s delve into some key aspects of cloud security in the context of cloud-native applications: 1. Securing Infrastructure as Code (IaC)Cloud-native applications embrace Infrastructure as Code (IaC) principles, allowing for the automated provisioning and management of cloud resources. By defining infrastructure configurations as code, organizations can ensure consistency and security across their cloud environment. They can apply security best practices, such as secure network configurations, access controls, and encryption, directly in their infrastructure code using tools like Terraform or Google Cloud Deployment Manager. 2. Immutable InfrastructureCloud-native applications adopt the concept of immutable infrastructure, where instances are never modified but replaced with new instances as updates or changes are required. This approach reduces the attack surface, as any compromised instances can be discarded and replaced with fresh, secure instances. Continuous integration and continuous deployment (CI/CD) pipelines ensure the seamless deployment of new instances, minimizing downtime and enhancing security. 3. Microservices Architecture
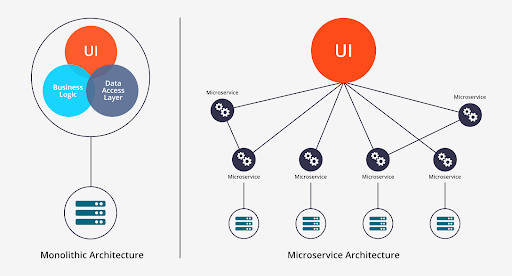
Cloud-native applications often embrace a microservices architecture, one of the key parts of cloud solutions offered by cloud service providers, where applications are broken into small, loosely coupled services. This architecture enhances security by isolating services, making it easier to apply fine-grained access controls and reducing the impact of potential security breaches. Each microservice can have its own authentication and authorization mechanisms, ensuring that access is granted on a need-to-know basis. 4. Zero Trust NetworkingCloud-native applications implement zero-trust networking principles to mitigate potential security threats. With zero trust, every request is treated as potentially malicious, regardless of its source or network location. Identity and access controls are enforced at every layer, from user authentication to service-to-service communication. Tools like Google Cloud Identity-Aware Proxy (IAP) and Cloud Armor provide robust mechanisms for implementing zero-trust networking within cloud-native architectures. 5. Cloud-Native Security Tools on GCPGCP offers a rich set of tools that empower organizations to enhance the security of their cloud-native applications. These tools include:
Use Case: Secure Customer Data Management with Cloud-Native ApplicationsImagine a SaaS company that offers a customer relationship management (CRM) platform, handling sensitive customer data. Say that they seek the help of one of the best cloud service providers to ensure the utmost security and compliance and the company leverages cloud-native applications empowered by various Google Cloud Platform (GCP) tools. Let’s explore how they achieve robust data protection. Data Encryption with Google Cloud KMS The SaaS company utilizes Google Cloud Key Management Service (KMS) to encrypt sensitive customer data at rest and in transit. By generating and managing encryption keys, they maintain full control over data confidentiality. With KMS integration, the application encrypts data before storing it in Google Cloud Storage, ensuring that only authorized entities can access and decrypt it. Identity and Access Management with Cloud IAM To implement fine-grained access controls and enforce the principle of least privilege, the SaaS company utilizes Google Cloud Identity and Access Management (IAM). They define granular access policies, granting appropriate permissions to different user roles. As one of the primary modern approaches in cyber security services, this ensures that only authorized personnel can access customer data and perform critical operations within the application. Secure Communication with Google Cloud VPN To establish secure connections between on-premises systems and cloud resources, the SaaS company employs Google Cloud VPN. This encrypted tunnel provides a secure and private channel for data transmission, preventing unauthorized access or interception. By integrating Cloud VPN into their cloud-native application architecture, they ensure secure communication between the CRM platform and external systems. Vulnerability Scanning with Google Cloud Security Scanner To proactively identify security weaknesses within their application code, the SaaS company utilizes Google Cloud Security Scanner. This tool automatically scans the application for common vulnerabilities, such as cross-site scripting (XSS) and SQL injection. By integrating regular security scans into their development pipeline, they can identify and address potential vulnerabilities before they can be exploited. Security Analytics with Google Cloud Security Command Center The SaaS company leverages Google Cloud Security Command Center to gain comprehensive visibility into its cloud-native application’s security posture. This centralized security management tool provides insights into potential security risks, alerts on suspicious activities, and offers recommendations for remediation. With this holistic view, they can proactively address security issues and ensure continuous compliance. Final Thoughts
Whether it’s data encryption, access controls, secure communication, vulnerability scanning, or security analytics, cloud-native applications built on cutting-edge solutions offered by cloud service providers in USA can empower businesses to protect their assets and ensure the trust of their customers. “In the realm of cloud-native applications, security is not just a feature, but a fundamental design principle that drives trust and confidence.” – A Cloud Security Enthusiast. | |